Describe Two Ways That Incident Data Is Used
Incident Recovery is conducted after the incident has been. Describe TWO conservation measures other than reducing hot water use that the family.

Cybersecurity Glossary Infographic Via Uk S National Cybersecurity Centre Malware Phishing Databreach Rans Computer Security Cyber Security Infographic
An alert roster is a document that includes contact information on every individual to be notified on the occasion of an actual incident.

. Simply put data exfiltration indicates the movement of sensitive data from inside the organization to outside without authorization. 1 point for identifying a specific number 185 million gallons and 199 million gallons. Two hundred incident categories yes I have actually seen that is WAY too many.
Incident Reaction involves the response to an actual incident. The NCVS includes crimes both reported and not reported to law enforcement. The data obtained from these sources are used for research and.
The data wasnt password protected and as such cybercriminals could have been easily downloaded and exploited it according to the security firm. Pare that list down. Incident alerting takes place in this step although the timing may vary according to how incidents are identified or categorized.
Crime Data Sources in the United States. Uniform Crime Reports and the National Incident-Based Reporting System Two major sources of crime statistics commonly used in the United States are the Uniform Crime Reports UCR and the National Incident-Based Reporting System NIBRS. Define the term incident as used in the context of IRP How is it related to the from ITIA 1400 at Macomb Community College.
In addition to the previously mentioned elements in common to all data displays tables have column and row headings that identify the data type and any units of measurement that apply to all data in that column or rowA well-structured analytical table that. Additionally if incidents are minor details may be logged or notifications sent without an official alert. In manual data capture process the data is entered manually by an operator using input devices like keyboard touch screens mouse etc.
Sequentially and hierarchically. The collection of crime data in the United States is carried out through different approaches including Uniform Crime Reports and the National Incident-Based Reporting System which also act as the two primary sources of crime data for crime reporting. Describe TWO environmental problems that can result from oil spills in coastal areas.
Using live system acquisition locally or. Keeping incident records provides a broad spectrum of information about the circumstance as well as helps establish a better course of action for future incident prevention. Incident Notification Escalation.
Data collection thus has a proactive accident preven-tion function even. Random Access Memory RAM registry and caches. Describe the two ways they can be used.
Sources of Crime Data. Using the data in the graph above determine the maximum volume of oil estimated to have been spilled during the Deepwater Horizon BP incident. Include units b Describe.
A well-defined incident response plan IRP allows you. Law firm certain types of security incidents are on the rise. Patterns will emerge over time and youll start to see better IT reporting.
TWO environmental problems that can result from oil spills in coastal areas. Incident classification is used to help determine this. Incident Detection is determining whether an incident is caused by routine systems use or an actual incident.
Tables are commonly used for characterizing disease cases or other health events and are ideal for displaying numeric values. Notification of key personnel incident documentation and incident containment strategies. For keying in data in the form of figures or text into particular software such as Excel or any.
Describe two ways that status data is used Status data are details that are used from CIS 202 at ECPI University. The maximum volume of oil estimated to have been spilled during the Deepwater Horizon BP incident. Using the data in the graph above determine.
A thorough review of this list and even minor tweaks to it can go a long way toward improving your Incident Management process. Second the two programs measure an overlapping but nonidentical set of crimes. Using a hardware device like a write blocker in case you can take the system offline and remove the hard drive.
To gather data from the hard drive depending on the case there are normally three strategies to do a bit stream image. The BJS established the NCVS to provide previously unavailable information about crime including crime not reported to police victims and offenders. According to the 2019 Data Security Incident Response Report by BakerHostetler LLP a US.
Depending upon the procedure of collecting information the data capture process can be divided into two segments. Volatile data is data that exists when the system is on and erased when powered off eg. Operating systems and applications can always be reinstalled but your data is unique--making it the most important thing on your computer or network.
There are two different types of data that can be collected in a computer forensics investigation. This can either be done accidentally or deliberately. There are many ways of organizing the information but all processes should rely as much as possible on factual data rather than inference.
An alert roster is a list of individuals within the company who must be notified in the event of an incident. Malware infections rapidly spread ransomware can cause catastrophic damage and compromised accounts can be used for privilege escalation giving attackers access to more sensitive assets. However data loss has been used interchangeably with data breach since cybercriminals dont always give your information back or corrupt it in the hacking process.
Incident response IR is a structured methodology for handling security incidents breaches and cyber threats. They are volatile data and non-volatile data persistent data. 10 things you can do to protect your data.
An alert message is a scripted notification that provides just enough information for responders to know the status of the incident and what portion of the incident response plan they need to implement. There are two ways to activate an alert roster. Data loss is distinct from data unavailability which is primarily caused by power outages and from a data breach which refers to your data being stolen.
In a sequential roster a contact person is required to call each and every individual on the roaster. Trends in the causes of incidents. Using an incident response and forensic toolkit such as Helix that will be used to boot the system.
Obtaining the Correct Information. This information is used to prevent reoccurrence of similar accidents and to identify the underlying causes that may give rise to new types of accidents in the future. This can either be done accidentally or deliberately.

Incident Management It Process Wiki

Root Cause Analysis Software Excel Tools Excel Tutorials Analysis Excel
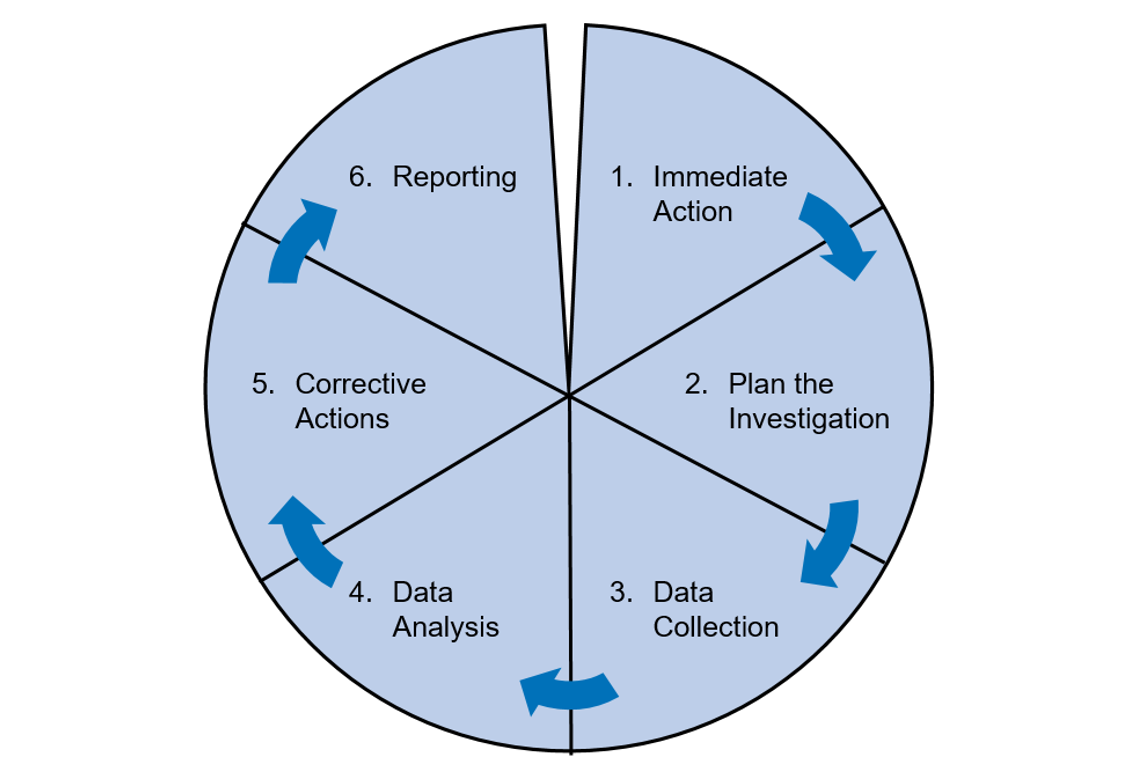
No comments for "Describe Two Ways That Incident Data Is Used"
Post a Comment